Your Hierarchical attribute based encryption algorithm images are ready. Hierarchical attribute based encryption algorithm are a topic that is being searched for and liked by netizens today. You can Download the Hierarchical attribute based encryption algorithm files here. Download all free vectors.
If you’re searching for hierarchical attribute based encryption algorithm images information related to the hierarchical attribute based encryption algorithm keyword, you have pay a visit to the ideal blog. Our site frequently gives you suggestions for viewing the highest quality video and image content, please kindly hunt and locate more enlightening video content and images that fit your interests.
Hierarchical Attribute Based Encryption Algorithm. Finally we propose a scalable revocation scheme. The layered access structures are integrated into a. Hierarchical attribute based encryption HABE is another important attribute based cryptographic primitive which extends ABE with key delegation. In this article we first propose a continuous auxiliary inputs leakage model for the hierarchical attributebased encryption scheme.
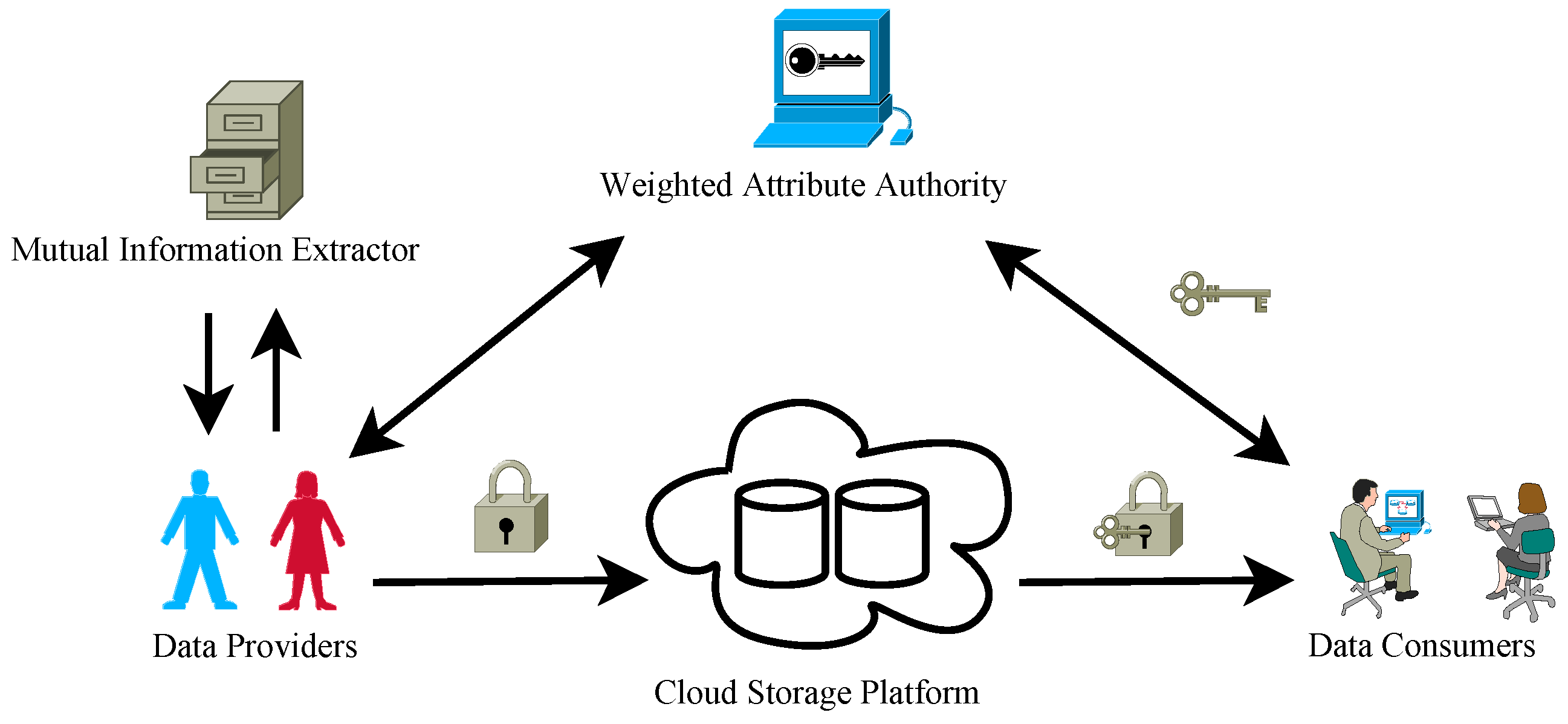 Applied Sciences Free Full Text Unified Ciphertext Policy Weighted Attribute Based Encryption For Sharing Data In Cloud Computing Html From mdpi.com
Applied Sciences Free Full Text Unified Ciphertext Policy Weighted Attribute Based Encryption For Sharing Data In Cloud Computing Html From mdpi.com
HASBE extends the cipher text- prove the security of the proposed scheme based on the policy attribute- set-based encryption CP-ASBE or ASBE. In this algorithm attribute based searching mechanism is used for searching data on cloud in which server is only allowed to learn the set of encrypted documents and attribute of the documents and not the keyword data. Balaji Chandrasekaran Student member ACM Ramadoss Balakrishnan Member IEEE and Yasuyuki Nogami Member IEEE. Two steps are required. The data owner encrypts a data with hisher own hierarchical attribute set. Third we formally control in cloud computing.
Based on the proposed CP-ABE algorithm we construct an Attribute-based Hierarchical data Access Control scheme AHAC in the cloud computing.
T he computation cost in generation of ciphertext is low and the length of the ciphertext is short. Hierarchical attribute based encryption HABE is another important attribute based cryptographic primitive which extends ABE with key delegation. Attribute-based encryption ABE has been envisioned as a promising cryptographic primitive for realizing secure and flexible access control. Attribute-Based Encryption for Fine-Grained Access Control of Encrypted Data Vipul Goyal Omkant Pandeyy Amit Sahaiz Brent Waters x Abstract As more sensitive data is shared and stored by third-party sites on the Internet there will be a need to encrypt data stored at these sites. In this paper we focus on improving the efficiency of ABE by leveraging a previously overlooked fact ie the. First the video is divided into segments according to resolution or time and encrypted by the advanced encryption.
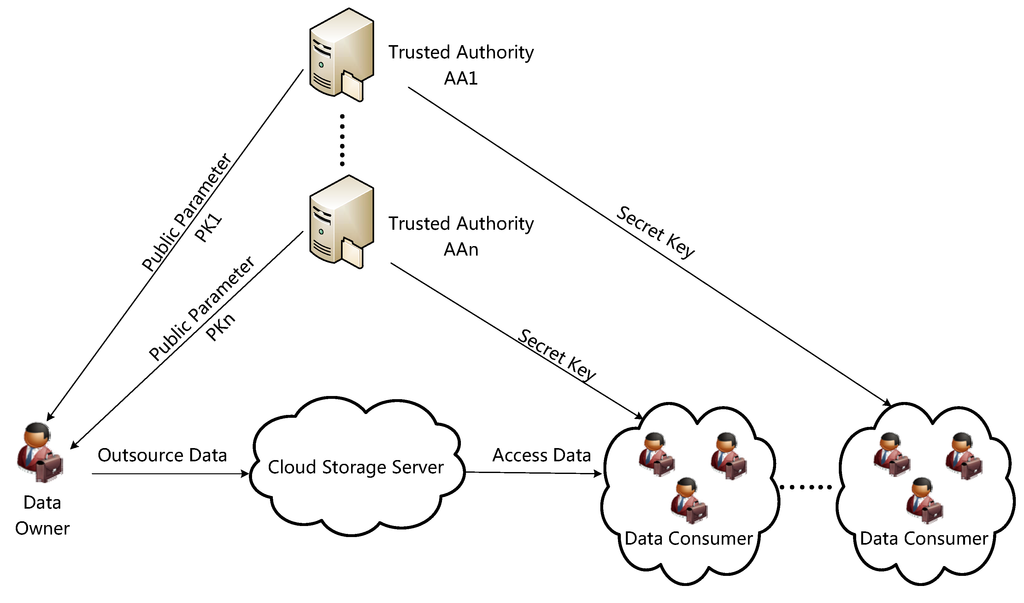 Source: mdpi.com
Source: mdpi.com
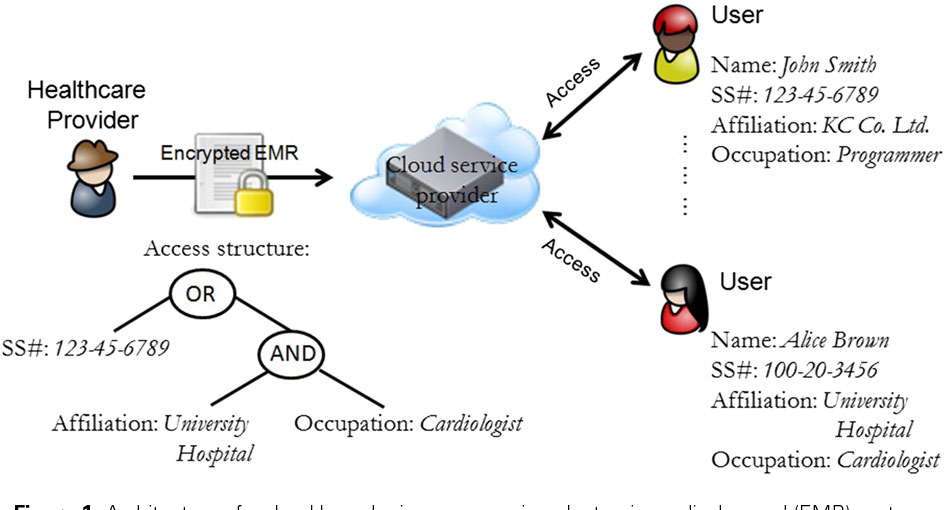
Balaji Chandrasekaran Student member ACM Ramadoss Balakrishnan Member IEEE and Yasuyuki Nogami Member IEEE. One drawback of encrypting data is that it can be selectively shared only at a coarse. Attribute-based encryption is a type of public-key encryption in which the secret key of a user and the ciphertext are dependent upon attributes. When a data visitors attributes match a part of the access control structure he can decrypt the data that associate with this part. In AHAC we achieve efficient and flexible access control.
 Source: mdpi.com
Source: mdpi.com
Attribute-based encryption is a type of public-key encryption in which the secret key of a user and the ciphertext are dependent upon attributes. Then eM-CP-ABE is applied to media cloud for fine-grained access control. In this system a ciphertext-policy attribute based encryption CP-ABE scheme by Bobba et al. When there are many attributes in the system HABE relieves the secret key generator from heavy key management burden. Proposed a hierarchical encryption scheme based on an identity-based encryption system and ciphertext policy attributes to solve the problem of fine-grained access control and proposed an extensible revocation scheme to effectively revoke user access rights.
 Source: researchgate.net
Source: researchgate.net
In this article we first propose a continuous auxiliary inputs leakage model for the hierarchical attributebased encryption scheme. A user in a. AbstractWireless Body Area Networks WBANs play an important role in healthcare system by enabling medical experts to guide patients remotely. Hierarchical attribute-based encryption HABE model by combining a HIBE system and a CP-ABE system to pro-vide fine-grained access control and full delegation. First the video is divided into segments according to resolution or time and encrypted by the advanced encryption.
 Source: researchgate.net
Source: researchgate.net
AbstractWireless Body Area Networks WBANs play an important role in healthcare system by enabling medical experts to guide patients remotely. Secure Data Communication using File Hierarchy Attribute Based Encryption in Wireless Body Area Networks. Based on the HABE model we construct a HABE scheme by making a performance-expressivity tradeoff to achieve high perfor-mance. In this paper we focus on improving the efficiency of ABE by leveraging a previously overlooked fact ie the. HABE under tree hierarchy the technique of hierarchical identity-based encryption is utilized in combination withthe secret sharing techniques in ABE.
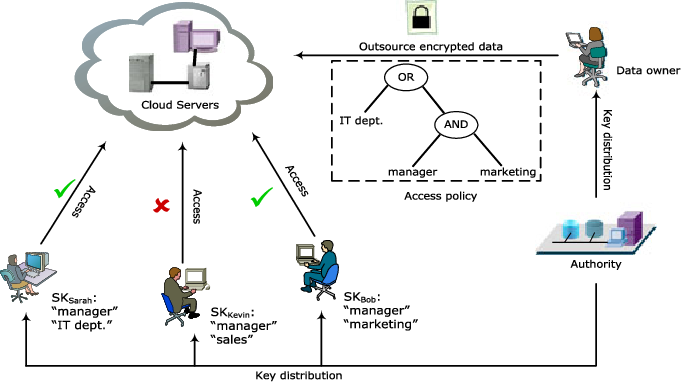 Source: semanticscholar.org
Source: semanticscholar.org
AbstractWireless Body Area Networks WBANs play an important role in healthcare system by enabling medical experts to guide patients remotely. In this section we mainly define about the proposed Ciphertext-Policy Attribute-Based Hierarchical document collection Encryption CP-ABHE algorithm for providing more security for the retrieval of sensitive documents from the cloud server. The data owner encrypts a data with hisher own hierarchical attribute set. In HABE users are associated with attribute vectors that denote their depth in the hierarchy. HABE under tree hierarchy the technique of hierarchical identity-based encryption is utilized in combination withthe secret sharing techniques in ABE.
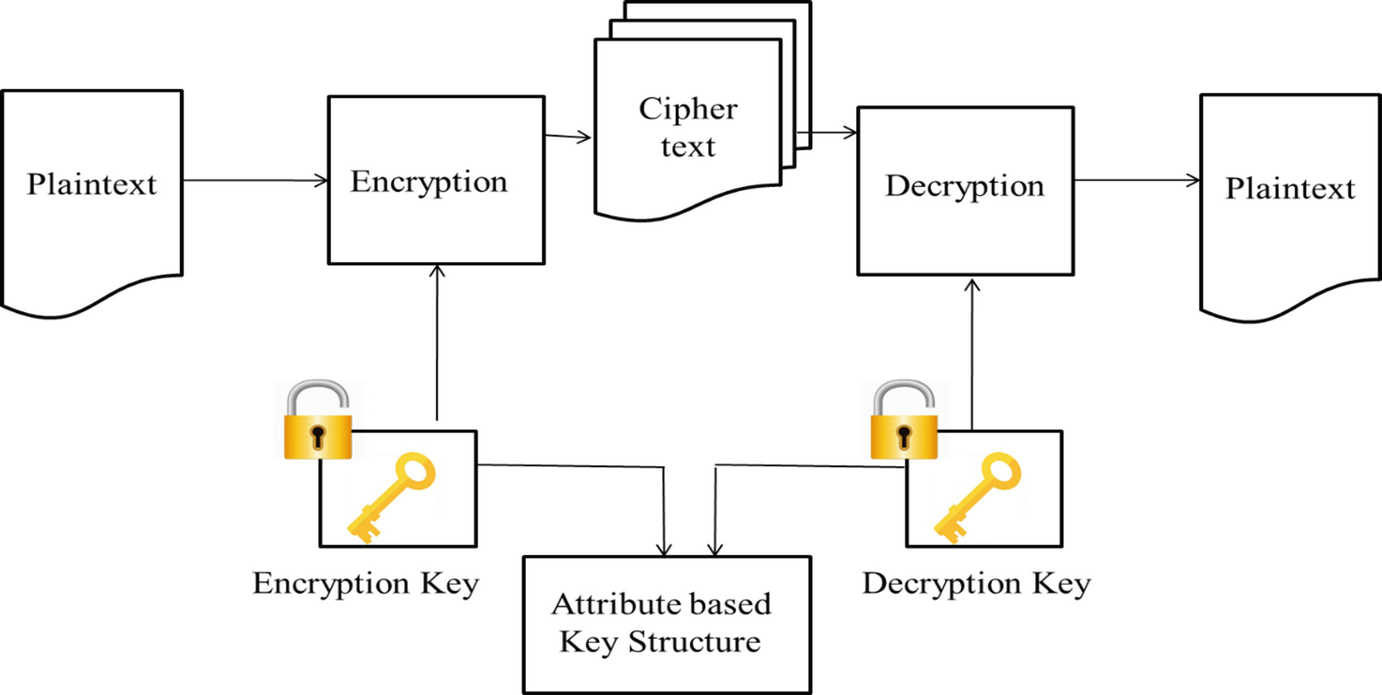 Source: link.springer.com
Source: link.springer.com
Third we formally control in cloud computing. However ABE is being criticized for its high scheme overhead as extensive pairing operations are usually required. Finally we propose a scalable revocation scheme. When there are many attributes in the system HABE relieves the secret key generator from heavy key management burden. The CP-HABE scheme is proved to be secure under the decisional q-parallel bilinear Diffie-Hellman exponent as-sumption which can be considered as the generalization of the traditional CP-ABE.
 Source: researchgate.net
Source: researchgate.net
In this algorithm attribute based searching mechanism is used for searching data on cloud in which server is only allowed to learn the set of encrypted documents and attribute of the documents and not the keyword data. However ABE is being criticized for its high scheme overhead as extensive pairing operations are usually required. Attribute-Based Encryption and Hierarchical Inner Product Encryption - Fully Secure Functional Encryption. Then eM-CP-ABE is applied to media cloud for fine-grained access control. Proposed a hierarchical encryption scheme based on an identity-based encryption system and ciphertext policy attributes to solve the problem of fine-grained access control and proposed an extensible revocation scheme to effectively revoke user access rights.
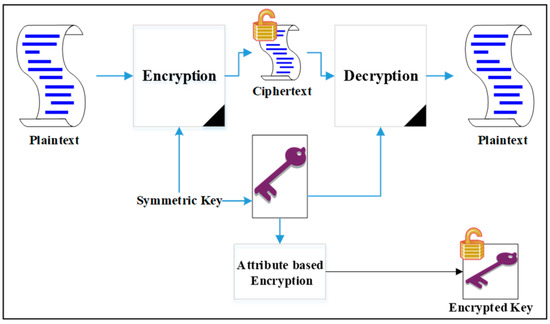 Source: mdpi.com
Source: mdpi.com
In this paper we focus on improving the efficiency of ABE by leveraging a previously overlooked fact ie the. In this paper we focus on improving the efficiency of ABE by leveraging a previously overlooked fact ie the. In such a system the decryption of a ciphertext is possible only if the set of attributes of the user key matches the attributes of the ciphertext. In HABE users are associated with attribute vectors that denote their depth in the hierarchy. Hierarchical Attribute based Encryption in Cloud Environment Sapana Kapadnis Computer Department MET BKC Adgaon NashikSavitribai Phule Pune University Maharashtra India.
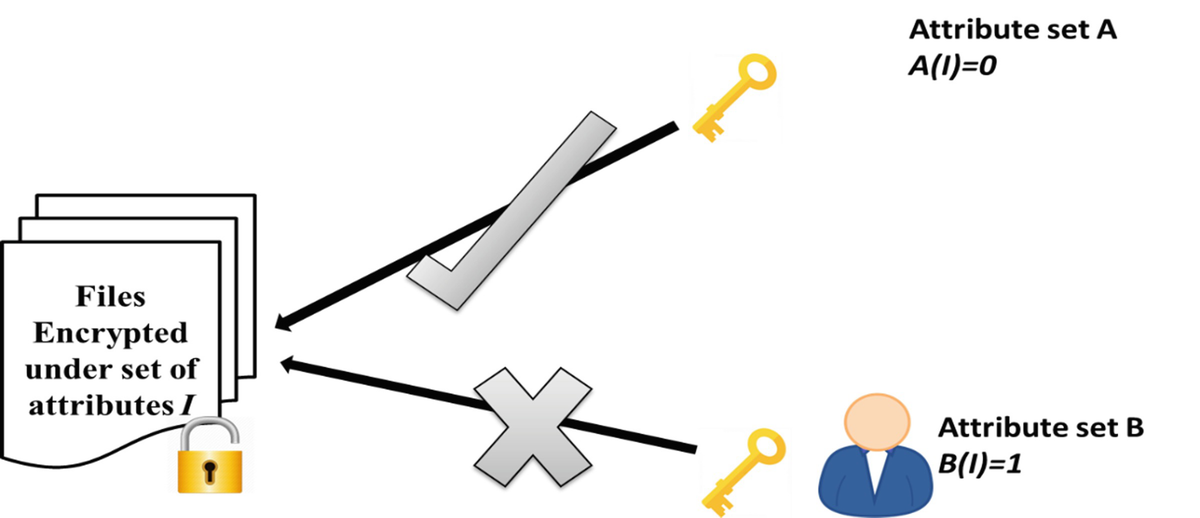 Source: link.springer.com
Source: link.springer.com
In a specific mobile cloud computing model enormous data which may be from all kinds of mobile devices such as smart phones functioned phones and. However ABE is being criticized for its high scheme overhead as extensive pairing operations are usually required. A crucial security aspect of attribute-based encryption is collusion-resistance. Third we formally control in cloud computing. Secure Data Communication using File Hierarchy Attribute Based Encryption in Wireless Body Area Networks.
 Source: researchgate.net
Source: researchgate.net
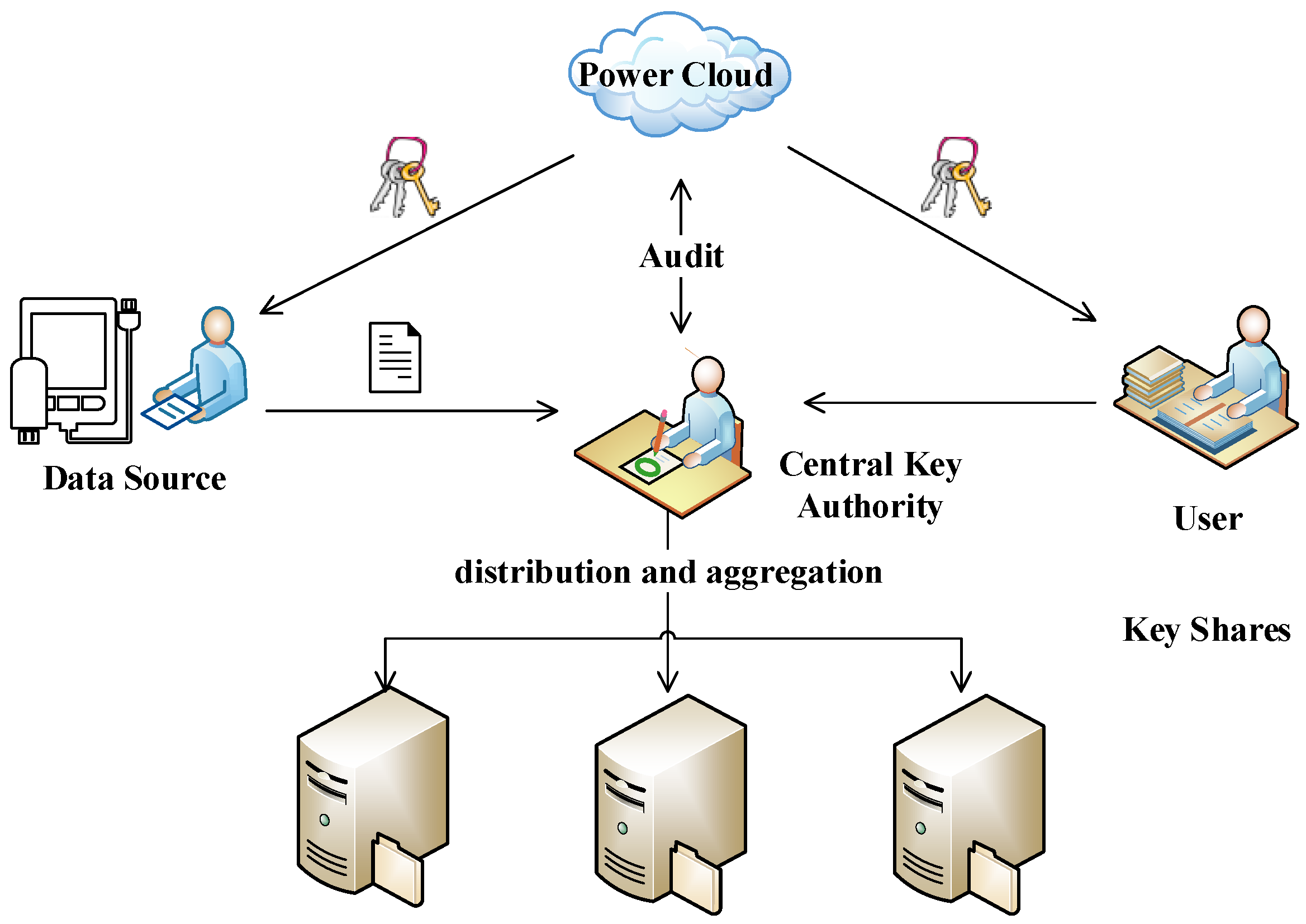
A modified hierarchical attribute based encryption m-habe access control method applied in mobile cloud computing is proposed in this paper which changes a. When there are many attributes in the system HABE relieves the secret key generator from heavy key management burden. In Section II the model for HABE. On the basis of these two components we introduce a novel enhanced-media Ciphertext-policy attribute-based encryption eM-CP-ABE algorithm. We propose a hierarchical hierarchical user grant filecreation file deletion and attribute-set-based encryption HASBE scheme for access user revocation in cloud computing.
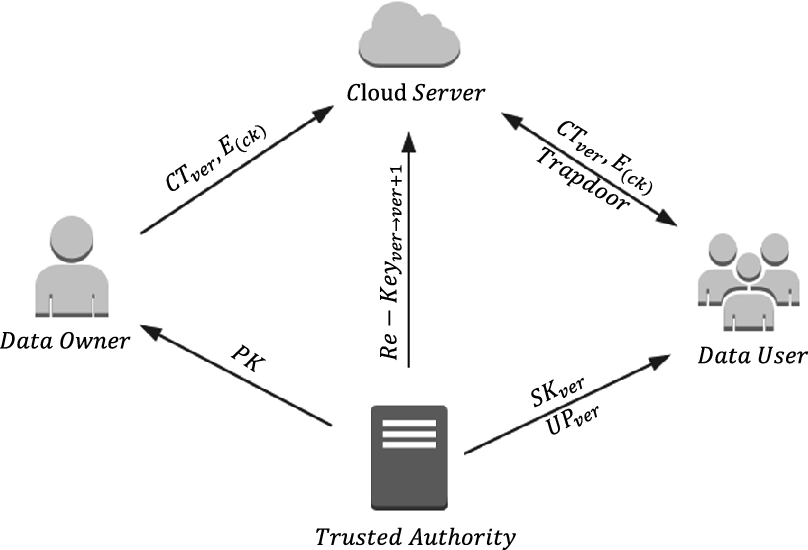 Source: link.springer.com
Source: link.springer.com
When a data visitors attributes match a part of the access control structure he can decrypt the data that associate with this part. When there are many attributes in the system HABE relieves the secret key generator from heavy key management burden. A users private key is associated with a set of attributes and ciphertext specifies an access policy over a. HABE under tree hierarchy the technique of hierarchical identity-based encryption is utilized in combination withthe secret sharing techniques in ABE. In Section II the model for HABE.

In this paper we focus on improving the efficiency of ABE by leveraging a previously overlooked fact ie the. ABSTRACT In the IT industry cloud computing is considered as one of the most important paradigms. In this system a ciphertext-policy attribute based encryption CP-ABE scheme by Bobba et al. A users private key is associated with a set of attributes and ciphertext specifies an access policy over a. Attribute-based encryption ABE has been envisioned as a promising cryptographic primitive for realizing secure and flexible access control.
 Source: sciencedirect.com
Source: sciencedirect.com
US10211984B2 US14348222 US201214348222A US10211984B2 US 10211984 B2 US10211984 B2 US 10211984B2 US 201214348222 A US201214348222 A US 201214348222A US 10211984 B2 US10211984 B2. In this system a ciphertext-policy attribute based encryption CP-ABE scheme by Bobba et al. Hierarchical attribute-based encryption HABE model by combining a HIBE system and a CP-ABE system to pro-vide fine-grained access control and full delegation. In this algorithm attribute based searching mechanism is used for searching data on cloud in which server is only allowed to learn the set of encrypted documents and attribute of the documents and not the keyword data. When a data visitors attributes match a part of the access control structure he can decrypt the data that associate with this part.
 Source: semanticscholar.org
Source: semanticscholar.org
Iii We show through detailed analysis that our construction is very efficient. The CP-HABE scheme is proved to be secure under the decisional q-parallel bilinear Diffie-Hellman exponent as-sumption which can be considered as the generalization of the traditional CP-ABE. A user in a. Attribute-based encryption is a type of public-key encryption in which the secret key of a user and the ciphertext are dependent upon attributes. Under the security model an adversary has ability to gain partial updated master keys and updated secret keys continually by certain leakage attacks.
 Source: mdpi.com
Source: mdpi.com
On the basis of these two components we introduce a novel enhanced-media Ciphertext-policy attribute-based encryption eM-CP-ABE algorithm. US10211984B2 US14348222 US201214348222A US10211984B2 US 10211984 B2 US10211984 B2 US 10211984B2 US 201214348222 A US201214348222 A US 201214348222A US 10211984 B2 US10211984 B2. Fully Secure Functional Encryption. Moreover a resilientleakage hierarchical attributebased encryption scheme is. One drawback of encrypting data is that it can be selectively shared only at a coarse.
 Source: mdpi.com
Source: mdpi.com
HABE under tree hierarchy the technique of hierarchical identity-based encryption is utilized in combination withthe secret sharing techniques in ABE. Balaji Chandrasekaran Student member ACM Ramadoss Balakrishnan Member IEEE and Yasuyuki Nogami Member IEEE. However ABE is being criticized for its high scheme overhead as extensive pairing operations are usually required. 19 with a hierarchical structure of system users where encryptions perform by. Hierarchical attribute based encryption HABE is another important attribute based cryptographic primitive which extends ABE with key delegation.
 Source: mdpi.com
Source: mdpi.com
Attribute-Based Encryption and Hierarchical Inner Product Encryption Allison Lewko Tatsuaki Okamoto Amit Sahai PowerPoint PPT presentation free to view. Third we formally control in cloud computing. Attribute-Based Encryption for Fine-Grained Access Control of Encrypted Data Vipul Goyal Omkant Pandeyy Amit Sahaiz Brent Waters x Abstract As more sensitive data is shared and stored by third-party sites on the Internet there will be a need to encrypt data stored at these sites. A crucial security aspect of attribute-based encryption is collusion-resistance. US10211984B2 US14348222 US201214348222A US10211984B2 US 10211984 B2 US10211984 B2 US 10211984B2 US 201214348222 A US201214348222 A US 201214348222A US 10211984 B2 US10211984 B2.
 Source: link.springer.com
Source: link.springer.com
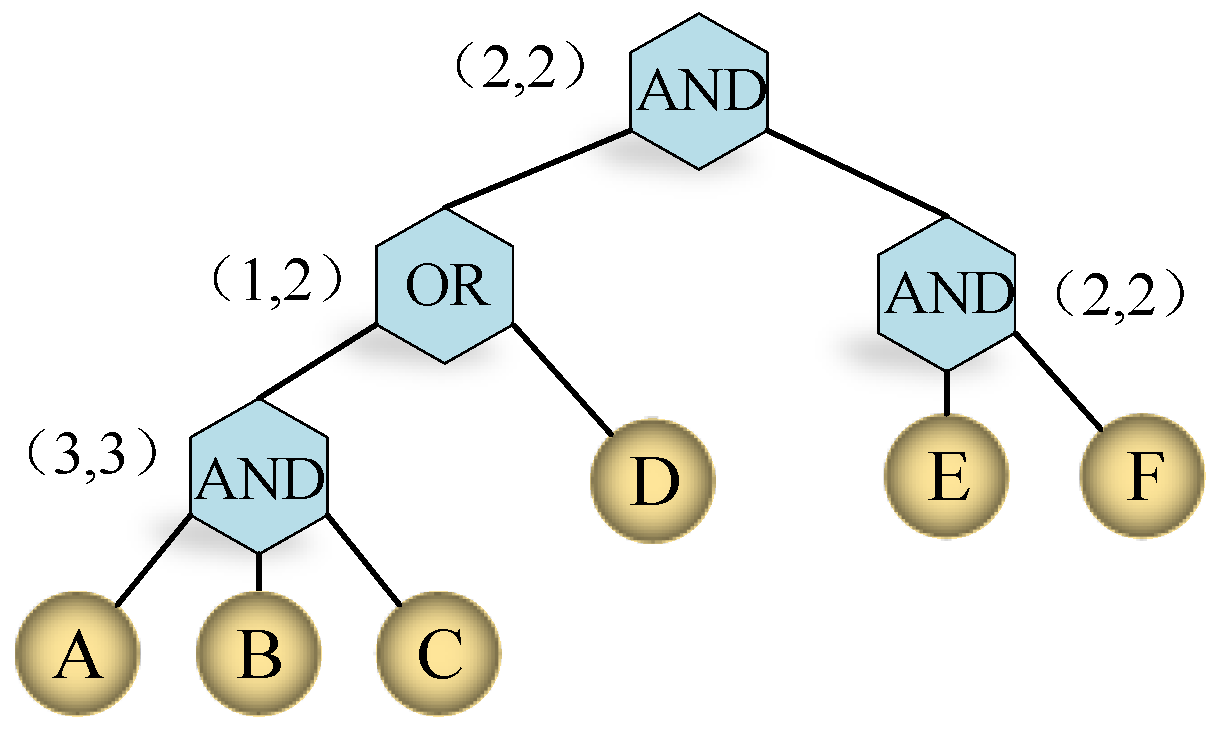
Then eM-CP-ABE is applied to media cloud for fine-grained access control. In a specific mobile cloud computing model enormous data which may be from all kinds of mobile devices such as smart phones functioned phones and. When there are many attributes in the system HABE relieves the secret key generator from heavy key management burden. In such a system the decryption of a ciphertext is possible only if the set of attributes of the user key matches the attributes of the ciphertext. In order to decrypt the message successfully the level of users attributes positions in the higher level of the private keys must be higher than the corresponding ones that in the lower level and the total number of this difference must exceed the threshold t.
This site is an open community for users to do sharing their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site beneficial, please support us by sharing this posts to your favorite social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title hierarchical attribute based encryption algorithm by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.