Your Hierarchical attribute based encryption images are ready. Hierarchical attribute based encryption are a topic that is being searched for and liked by netizens today. You can Find and Download the Hierarchical attribute based encryption files here. Get all free images.
If you’re looking for hierarchical attribute based encryption pictures information related to the hierarchical attribute based encryption topic, you have visit the ideal site. Our website always provides you with hints for seeking the highest quality video and picture content, please kindly hunt and find more enlightening video content and graphics that match your interests.
Hierarchical Attribute Based Encryption. We propose a hierarchical hierarchical user grant filecreation file deletion and attribute-set-based encryption HASBE scheme for access user revocation in cloud computing. The scheme is obviously not practical. File hierarchy attribute based encryption FH-CP-ABE is a scheme which both saves storage space of ciphertext and reduces the computation overhead of encryption. Ciphertext-policy hierarchical attribute based encryption.

T he computation cost in generation of ciphertext is low and the length of the ciphertext is short. Hierarchical attribute based encryption with continuous leakage-resilience 1. Attribute-Based Encryption and Hierarchical Inner Product Encryption - Fully Secure Functional Encryption. With system users having hierarchical structure to achieve flexible scalable and fine grained access control. Based on the HABE model we construct a HABE scheme by making a performance-expressivity tradeoff to achieve high perfor-mance. Moreover a resilientleakage hierarchical attributebased encryption scheme is.
In order to achieve scalable fine-grained and flexible access control for cloud computing we extends Ciphertext-Policy Attribute-Set-Based Encryption CP-ASBE by building in a hierarchical structure to obtain Hierarchical Attribute-Set-Based Encryption HASBE for cloud computing.
File hierarchy attribute based encryption FH-CP-ABE is a scheme which both saves storage space of ciphertext and reduces the computation overhead of encryption. In this section we introduce some required preliminaries. First we propose a hierarchical attribute-based encryption scheme HABE by combining a hierarchical identity-based encryption HIBE system and a ciphertext-policy attribute-based encryption CP-ABE system so as to provide not only fine-grained access control but also full delegation and high performance. In order to achieve scalable fine-grained and flexible access control for cloud computing we extends Ciphertext-Policy Attribute-Set-Based Encryption CP-ASBE by building in a hierarchical structure to obtain Hierarchical Attribute-Set-Based Encryption HASBE for cloud computing. HASBE extends the cipher text- prove the security of the proposed scheme based on the policy attribute- set-based encryption CP-ASBE or ASBE. We propose a hierarchical hierarchical user grant filecreation file deletion and attribute-set-based encryption HASBE scheme for access user revocation in cloud computing.
 Source: researchgate.net
Source: researchgate.net
Moreover a resilientleakage hierarchical attributebased encryption scheme is. Based on the proposed CP-ABE algorithm we construct an Attribute-based Hierarchical data Access Control scheme AHAC in the cloud computing. Based on the HABE model we construct a HABE scheme by making a performance-expressivity tradeoff to achieve high perfor-mance. US10211984B2 US14348222 US201214348222A US10211984B2 US 10211984 B2 US10211984 B2 US 10211984B2 US 201214348222 A US201214348222 A US 201214348222A US 10211984 B2 US10211984 B2. First we propose a hierarchical attribute-based encryption scheme HABE by combining a hierarchical identity-based encryption HIBE system and a ciphertext-policy attribute-based encryption CP-ABE system so as to provide not only fine-grained access control but also full delegation and high performance.
 Source: sciencedirect.com
Source: sciencedirect.com
In this section we introduce some required preliminaries. Third we formally control in cloud computing. In this paper we focus on improving the efficiency of ABE by leveraging a previously overlooked fact ie the. According to the relation of an attribute set and its subset the author presents a hierarchical attribute-based encryption scheme in which a secret key is. Attribute-based encryption ABE has been envisioned as a promising cryptographic primitive for realizing secure and flexible access control.
 Source: semanticscholar.org
Source: semanticscholar.org
Moreover the size of the. A fully distributed hierarchical attribute-based encryption scheme 1. However ABE is being criticized for its high scheme overhead as extensive pairing operations are usually required. The CP-HABE scheme is proved to be secure under the decisional q-parallel bilinear Diffie-Hellman exponent as-sumption which can be considered as the generalization of the traditional CP-ABE. Hierarchical attribute based encryption with continuous leakage-resilience 1.
 Source: semanticscholar.org
Source: semanticscholar.org
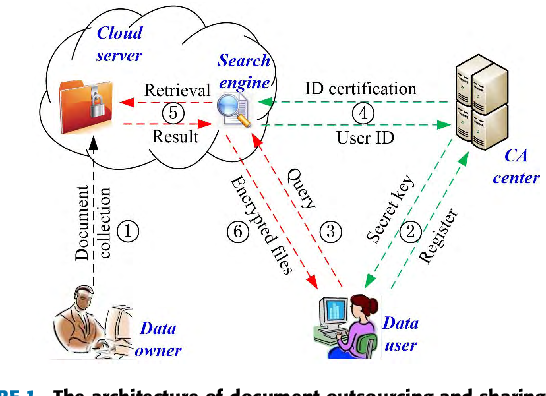
HIERARCHICAL ATTRIBUTE SET BASED ENCRYPTION HASBEHASBE extends the cipher text-policy attribute-set-based encryption CP-ASBE or ASBE for short scheme proposed by Bobba et al9. In this section we introduce some required preliminaries. HASBE extends the cipher text- prove the security of the proposed scheme based on the policy attribute- set-based encryption CP-ASBE or ASBE. Therefore one same data has to be encrypted into ciphertext once which ought to be able to be decrypted multiple times by different authorized users. Based on the proposed CP-ABE algorithm we construct an Attribute-based Hierarchical data Access Control scheme AHAC in the cloud computing.
 Source: link.springer.com
Source: link.springer.com
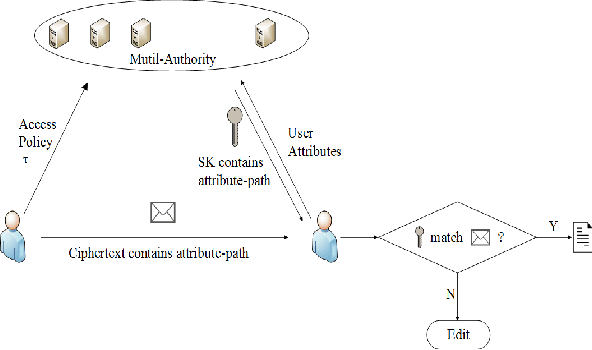
In Section II the model for HABE. Moreover a resilientleakage hierarchical attributebased encryption scheme is. When a data visitors attributes match a part of the access control structure he can decrypt the data that associate with this part. First we propose a hierarchical attribute-based encryption scheme HABE by combining a hierarchical identity-based encryption HIBE system and a ciphertext-policy attribute-based encryption CP-ABE system so as to provide not only fine-grained access control but also full delegation and high performance. Fully Secure Functional Encryption.

In this paper a hierarchical access control method using a modified hierarchical attribute-based encryption M-HABE and a modified three-layer structure is proposed. Attribute-based encryption ABE has been envisioned as a promising cryptographic primitive for realizing secure and flexible access control. Its an emerging but promising paradigm to integrating mobile devices. File hierarchy attribute based encryption FH-CP-ABE is a scheme which both saves storage space of ciphertext and reduces the computation overhead of encryption. HIERARCHICAL ATTRIBUTE SET BASED ENCRYPTION HASBEHASBE extends the cipher text-policy attribute-set-based encryption CP-ASBE or ASBE for short scheme proposed by Bobba et al9.
 Source: mdpi.com
Source: mdpi.com
When a data visitors attributes match a part of the access control structure he can decrypt the data that associate with this part. Moreover a resilientleakage hierarchical attributebased encryption scheme is. HASBE extends the cipher text- prove the security of the proposed scheme based on the policy attribute- set-based encryption CP-ASBE or ASBE. When a data visitors attributes match a part of the access control structure he can decrypt the data that associate with this part. Finally we propose a scalable revocation scheme.

In this paper we focus on improving the efficiency of ABE by leveraging a previously overlooked fact ie the. We propose a hierarchical hierarchical user grant filecreation file deletion and attribute-set-based encryption HASBE scheme for access user revocation in cloud computing. Proposed a hierarchical encryption scheme based on an identity-based encryption system and ciphertext policy attributes to solve the problem of fine-grained access control and proposed an extensible revocation scheme to effectively revoke user access rights. Therefore one same data has to be encrypted into ciphertext once which ought to be able to be decrypted multiple times by different authorized users. The security of modern cryptosystems is mainly based on black box model where the only access to the.
 Source: semanticscholar.org
Source: semanticscholar.org
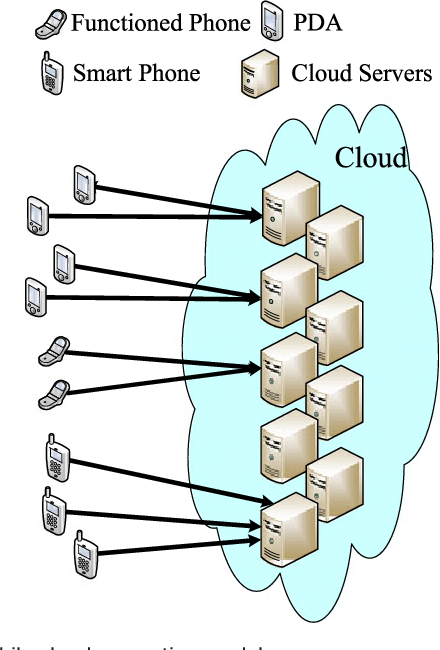
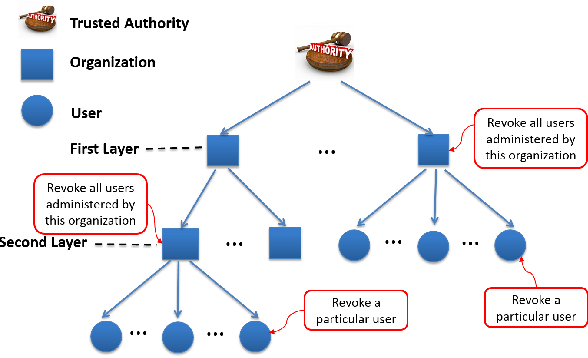
Third we formally control in cloud computing. Finally we propose a scalable revocation scheme. File hierarchy attribute based encryption FH-CP-ABE is a scheme which both saves storage space of ciphertext and reduces the computation overhead of encryption. A Modified Hierarchical Attribute-Based Encryption Access Control Method for Mobile Cloud Computing Yuanpeng Xie Hong Wen Bin Wu Yixin Jiang and Jiaxiao Meng AbstractCloud computing is an Internet-based computing pattern through which shared resources are provided to devices on-demand. Its an emerging but promising paradigm to integrating mobile devices.
 Source: link.springer.com
Source: link.springer.com
HABE under tree hierarchy the technique of hierarchical identity-based encryption is utilized in combination withthe secret sharing techniques in ABE. With the widespread applications of cloud computing technology it is increasingly evolving to change. In Section II the model for HABE. Therefore one same data has to be encrypted into ciphertext once which ought to be able to be decrypted multiple times by different authorized users. Its an emerging but promising paradigm to integrating mobile devices.

The security of modern cryptosystems is mainly based on black box model where the only access to the. Proposed a hierarchical encryption scheme based on an identity-based encryption system and ciphertext policy attributes to solve the problem of fine-grained access control and proposed an extensible revocation scheme to effectively revoke user access rights. However ABE is being criticized for its high scheme overhead as extensive pairing operations are usually required. With system users having hierarchical structure to achieve flexible scalable and fine grained access control. Therefore one same data has to be encrypted into ciphertext once which ought to be able to be decrypted multiple times by different authorized users.
 Source: link.springer.com
Source: link.springer.com
Based on the proposed CP-ABE algorithm we construct an Attribute-based Hierarchical data Access Control scheme AHAC in the cloud computing. In Section II the model for HABE. First we propose a hierarchical attribute-based encryption scheme HABE by combining a hierarchical identity-based encryption HIBE system and a ciphertext-policy attribute-based encryption CP-ABE system so as to provide not only fine-grained access control but also full delegation and high performance. The proposed scheme inherits flexibility in supporting compound attributes and. A Modified Hierarchical Attribute-Based Encryption Access Control Method for Mobile Cloud Computing Yuanpeng Xie Hong Wen Bin Wu Yixin Jiang and Jiaxiao Meng AbstractCloud computing is an Internet-based computing pattern through which shared resources are provided to devices on-demand.
 Source: semanticscholar.org
Source: semanticscholar.org
Moreover the size of the. Under the security model an adversary has ability to gain partial updated master keys and updated secret keys continually by certain leakage attacks. Hierarchical attribute-based encryption HABE model by combining a HIBE system and a CP-ABE system to pro-vide fine-grained access control and full delegation. A Modified Hierarchical Attribute-Based Encryption Access Control Method for Mobile Cloud Computing Yuanpeng Xie Hong Wen Bin Wu Yixin Jiang and Jiaxiao Meng AbstractCloud computing is an Internet-based computing pattern through which shared resources are provided to devices on-demand. However its impossible to encrypt multiple files on the same access level in existing FH-CP-ABE scheme.
 Source: researchgate.net
Source: researchgate.net
HABE under tree hierarchy the technique of hierarchical identity-based encryption is utilized in combination withthe secret sharing techniques in ABE. US10211984B2 US14348222 US201214348222A US10211984B2 US 10211984 B2 US10211984 B2 US 10211984B2 US 201214348222 A US201214348222 A US 201214348222A US 10211984 B2 US10211984 B2. According to the relation of an attribute set and its subset the author presents a hierarchical attribute-based encryption scheme in which a secret key is associated with an attribute set. Ciphertext-policy hierarchical attribute based encryption. Moreover the size of the.
 Source: semanticscholar.org
Source: semanticscholar.org
According to the relation of an attribute set and its subset the author presents a hierarchical attribute-based encryption scheme in which a secret key is associated with an attribute set. With the widespread applications of cloud computing technology it is increasingly evolving to change. Its an emerging but promising paradigm to integrating mobile devices. Fully Secure Functional Encryption. According to the relation of an attribute set and its subset the author presents a hierarchical attribute-based encryption scheme in which a secret key is.
 Source: semanticscholar.org
Source: semanticscholar.org
With the widespread applications of cloud computing technology it is increasingly evolving to change. Attribute-Based Encryption and Hierarchical Inner Product Encryption - Fully Secure Functional Encryption. According to the relation of an attribute set and its subset the author presents a hierarchical attribute-based encryption scheme in which a secret key is. US10211984B2 US14348222 US201214348222A US10211984B2 US 10211984 B2 US10211984 B2 US 10211984B2 US 201214348222 A US201214348222 A US 201214348222A US 10211984 B2 US10211984 B2. According to the relation of an attribute set and its subset the author presents a hierarchical attribute-based encryption scheme in which a secret key is associated with an attribute set.
 Source: semanticscholar.org
Source: semanticscholar.org
Attribute-based encryption system private keys distributed by an authority are associated with sets of attributes and ciphertexts are associated with formulas over attributes. Fully Secure Functional Encryption. Attribute-based encryption system private keys distributed by an authority are associated with sets of attributes and ciphertexts are associated with formulas over attributes. First we propose a hierarchical attribute-based encryption scheme HABE by combining a hierarchical identity-based encryption HIBE system and a ciphertext-policy attribute-based encryption CP-ABE system so as to provide not only fine-grained access control but also full delegation and high performance. In this paper an efficient extended file hierarchy CP.
 Source: semanticscholar.org
Source: semanticscholar.org
HIERARCHICAL ATTRIBUTE SET BASED ENCRYPTION HASBEHASBE extends the cipher text-policy attribute-set-based encryption CP-ASBE or ASBE for short scheme proposed by Bobba et al9. The proposed scheme inherits flexibility in supporting compound attributes and. With system users having hierarchical structure to achieve flexible scalable and fine grained access control. In Section II the model for HABE. Third we formally control in cloud computing.
This site is an open community for users to do submittion their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site adventageous, please support us by sharing this posts to your preference social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title hierarchical attribute based encryption by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






